Requirement engineering aims to define a system’s purposes but if its main constituents specialize, then how can the purpose of the whole system be defined? The approach taken here is to specify the requirements for each constituent separately then leave how these requirements are reconciled in a specific environment to the art of system design.
In general, a system performs by interacting with its environment to gain value and avoid loss. In Darwinian terms, what does not survive dies out and what does lives on. Any system in this situation needs a boundary to separate it from the world, a structure to support its existence, effectors to act upon the environment around it, and receptors to monitor the world for risks and opportunities (see Table 2.2). The requirement to reproduce is here ignored as it is not relevant to computing and adds a time dimension to the model.
|
Constituent |
Requirement |
Definition |
|
Boundary |
Security |
To deny unauthorized entry, misuse or takeover by other entities. |
|
|
Extendibility |
To attach to or use outside elements as system extensions. |
|
Structure |
Flexibility |
To adapt system operation to new environments |
|
|
Reliability |
To continue operating despite system part failure |
|
Effector |
Functionality |
To produce a desired change on the environment |
|
|
Usability |
To minimize the resource costs of action |
|
Receptor |
Connectivity |
To open and use communication channels |
|
|
Privacy |
To limit the release of self-information by any channel |
Table 2.2: General system constituents and requirements
For example, cells first evolved a boundary membrane, then organelle and nuclear structures for support and control; then eukaryotic cells evolved flagella to move, and finally protozoa got photo-receptors (Alberts et al., 1994). We also have a skin boundary, internal structures for metabolism and control, muscle effectors and sense receptors. Computers also have a case boundary, a motherboard internal structure, printer or screen effectors and keyboard or mouse receptors.
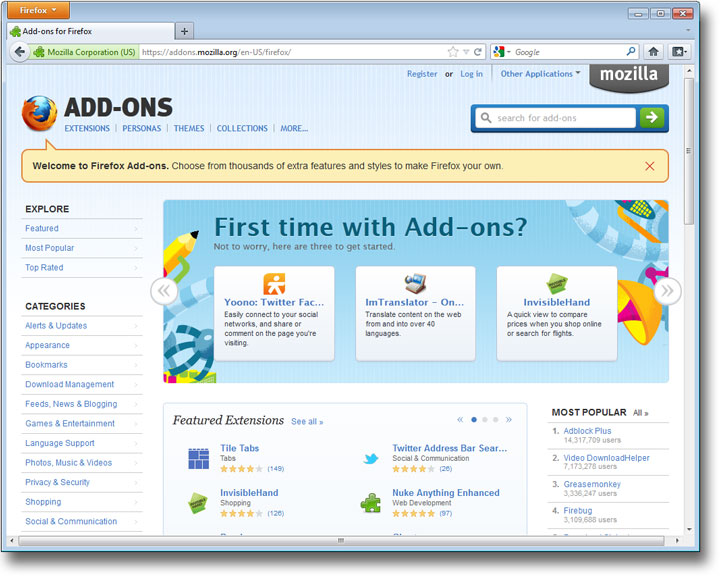
Four main constituents, each with risk and opportunity, gives eight general performance requirements as follows:
a) Boundary constituents manage the system boundary. They can be designed to deny outside things entry (security) or to use them (extendibility). In computing, virus protection is security and system add-ons are extendibility (Figure 2.2). In people, the immune system gives biological security and tool-use illustrates extendibility.
b) Structure constituents manage internal operations. They can be designed to limit internal change to reduce faults (reliability), or to allow internal change to adapt to outside changes (flexibility). In computing, reliability reduces and recovers from error, and flexibility is the system preferences that allow customization. In people, reliability is the body fixing a cell “error” that might cause cancer, while the brain learning illustrates flexibility.
c) Effector constituents manage environment actions, so can be designed to maximize effects (functionality) or minimize resource use (usability). In computing, functionality is the menu functions, while usability is how easy they are to use. In people, functionality gives muscle effectiveness, and usability is metabolic efficiency.
d) Receptor constituents manage signals to and from the environment, so can be designed to open communication channels (connectivity) or close them (privacy). Connected computing can download updates or chat online, while privacy is the power to disconnect or log off. In people, connectivity is conversing, and privacy is the legal right to be left alone. In nature, privacy is camouflage, and the military calls it stealth. Note that privacy is the ownership of self-data, not secrecy. It includes the right to make personal data public.
These eight general requirements map well to current requirements engineering terms (Table 2.3).
|
Requirement |
Requirements Engineering Synonyms |
|
Functionality |
Effectualness, capability, usefulness, effectiveness, power, utility. |
|
Usability |
Ease of use, simplicity, user friendliness, efficiency, accessibility. |
|
Extendibility |
Openness, interoperability, permeability, compatibility, standards. |
|
Security |
Defense, protection, safety, threat resistance, integrity, inviolable. |
|
Flexibility |
Adaptability, portability, customizability, plasticity, agility, modifiability. |
|
Reliability |
Stability, dependability, robustness, ruggedness, durability, availability. |
|
Connectivity |
Networkability, communicability, interactivity, sociability. |
|
Privacy |
Tempest proof, confidentiality, secrecy, camouflage, stealth, encryption. |
Table 2.3: System requirement synonyms
Note that as what is exchanged changes by system level, so do the names preferred:
a) Hardware systems exchange energy. So for them functionality is often called power, e.g. hardware with a high CPU cycle rate. Usable hardware uses less power for the same result, e.g. mobile phones that last longer. Reliable hardware is rugged enough to work if you drop it, and flexible hardware is mobile enough to work if you move around, i.e. change environments. Secure hardware blocks physical theft, e.g. by laptop cable locks, and extendible hardware has ports for peripherals to be attached. Connected hardware has wired or wireless links and private hardware is tempest proof i.e. it does not physically leak energy.
b) Software systems exchange information. Functional software has many ways to process information, while usable software uses less CPU processing (“lite” apps). Reliable software avoids errors or recovers from them quickly. Flexible software is operating system platform independent. Secure software cannot be corrupted or overwritten. Extendible software can access OS program library calls. Connected software has protocol “handshakes” to open read/write channels. Private software can encrypt information so that others cannot see it.
c) HCI systems exchange meaning, including ideas, feelings and intents. In functional HCI the human computer pair is effectual, i.e. meets the user task goal. Usable HCI requires less intellectual, affective or conative effort, i.e. is intuitive. Note that cognitions divide into intellectual thoughts, affective emotions, and conative will. Reliable HCI avoids or recovers from unintended user errors by checks or undo choices — the web Back button is an HCI invention. Flexible HCI lets users change language, font size or privacy preferences, as each person is a new environment to the software. Secure HCI avoids identity theft by user password. Extendible HCI lets users use what others create, e.g. mash-ups and third–party add-ons. Connected HCI communicates with others, while privacy includes not getting spammed or being located on a mobile device. Each level applies the same ideas to a different system view. The community level is discussed in Chapter 3.