Based on the previous definition (Whitworth, 2005), polite software should:
- Respect the owner. Polite software respects owner rights, does not act preemptively, and does not change data without the permission of its owner.
- Be visible. Polite software does not sneak around changing things in secret, but openly declares what it is doing and who it represents.
- Be understandable. Polite software helps people make informed choices by giving information that is useful and understandable.
- Remember past interactions. Polite software remembers its past interactions and so carries forward your past choices to future interactions.
- Respond to you. Polite software responds to human directions rather than trying to pursue its own agenda.
1. Respect the user
Respect includes not taking another’s rightful choices. If two parties jointly share a resource, one party’s choices can deny the other’s; e.g. if I delete a shared file, you can no longer print it. Polite software should not preempt rightful user information choices regarding common resources such as the desktop, registry, hard drive, task bar, file associations, quick launch and other user configurable settings. Pre-emptive acts, like changing a browser home page without asking, act unilaterally on a mutual resource and so are impolite.
Information choice cases are rarely simple; e.g. a purchaser can use software but not edit, copy or distribute it. Such rights can be specified as privileges, in terms of specified information actors, methods, objects and contexts (see Chapter 6). To apply politeness in such cases requires a legitimacy baseline; e.g. a provider has no unilateral right to upgrade software on a computer the user owns (though the Microsoft Windows Vista End User License Agreement (EULA) seems to imply this). Likewise users have no right to alter the product source code unilaterally. In such cases politeness applies; e.g. the software suggests an update and the user agrees, or the user requests an update and the software agrees (for the provider). Similarly while a company that creates a browser owns it, the same logic means users own data they create with the browser, e.g. a cookie. Hence, software cookies require user permission to create, and users can view, edit or delete them.
2. Be visible
Part of a polite greeting in most cultures is to introduce oneself and state one’s business. Holding out an open hand, to shake hands, shows that the hand has no weapon, and that nothing is hidden. Conversely, to act secretly behind another’s back, to sneak, or to hide one’s actions, for any reason, is impolite. Secrecy in an interaction is impolite because the other has no choice regarding things they do not know about. Hiding your identity reduces my choices, as hidden parties are untouchable and unaccountable for their actions. When polite people interact, they declare who they are and what they are doing.
If polite people do this, polite software should do the same. Users should be able to see what is happening on their computer. Yet when Windows Task Manager attributes cryptic process like CTSysVol.exe to the user, it could be a system critical process or one left over from a long uninstalled product. Lack of transparency is why after 2-3 years Windows becomes “old”. With every installation of selfish software it puts itself everywhere, fills the taskbar with icons, the desktop with images, the disk with files and the registry with records. In the end, the computer owner has no idea what software is responsible for what files or registry records.
Selfish applications consider themselves important enough to load at start-up and run continuously, in case you need them. Many applications doing this slow down a computer considerably, whether on a mobile phone or a desktop. Taskbar icon growth is just the tip of the iceberg of what is happening to the computer, as some start-ups do not show on the taskbar. Selfish programs put files where they like, so uninstalled applications are not removed cleanly, and over time Windows accretes a “residue” of files and registry records left over from previous installs. Eventually, only reinstalling the entire operating system recovers system performance.
The problem is that the operating system keeps no transparent record of what applications do. An operating system Source Registry could link all processes to their social sources, giving contact and other details. Source could be a property of every desktop icon, context menu item, taskbar icon, hard drive file or any other resource. If each source creates its own resources, a user could then delete all resources allocated by a source they have uninstalled without concern that they were system critical. Windows messages could also state their source, so that users knew who a message was from. Application transparency would let users decide what to keep and what to drop.
3. Be Understandable
A third politeness property is to help the user by offering understandable choices, as a user cannot properly choose from options they do not understood. Offering options that confuse is inconsiderate and impolite, e.g. a course text web site offers the choices:
- OneKey Course Compass
- Content Tour
- Companion Website
- Help Downloading
- Instructor Resource Centre
It is unclear how the “Course Compass” differs from the “Companion Website”, and why both seem to exclude “Instructor Resources” and “Help Downloading”. Clicking on these choices, as is typical for such sites, leads only to further confusing menu choices. The impolite assumption is that users enjoy clicking links to see where they go. Yet information overload is a serious problem for web users, who have no time for hyperlink merry-go-rounds.
Not to offer choices at all on the grounds that users are too stupid to understand them is also impolite. Installing software can be complex, but so is installing satellite TV technology, and those who install the latter do not just come in and take over. Satellite TV installers know that the user who pays expects to hear his or her choices presented in an understandable way. If not, the user may decide not to have the technology installed.
Complex installations are simplified by choice dependency analysis, of how choices are linked, as Linux’s installer does. Letting a user choose to install an application the user wants minus a critical system component is not a choice but a trap. Application-critical components are part of the higher choice to install or not; e.g. a user’s permission to install an application may imply access to hard drive, registry and start menu, but not to desktop, system tray, favorites or file associations.
4. Remember past interactions
It is not enough for the software to give choices now but forget them later. If previous responses have been forgotten, the user is forced to restate them, which is inconsiderate. Software that actually listens and remembers past user choices is a wonderful thing. Polite people remember previous encounters, but each time Explorer opens it fills its preferred directory with files I do not want to see, and then asks me which directory I want, which is never the one displayed. Each time I tell it, and each time Explorer acts as if it were the first time I had used it. Yet I am the only person it has ever known. Why can’t it remember the last time and return me there? The answer is that it is impolite by design.
Such “amnesia” is a trademark of impolite software. Any document editing software could automatically open a user’s last open document, and put the cursor where they left off, or at least give that option (Raskin, 2000, p.31). The user logic is simple: If I close the file I am finished, but if I just exit without closing the document, then put me back where I was last time. It is amazing that most software cannot even remember the last user interaction. Even within an application, like email, if one moves from inbox to outbox and back, it “forgets” the original inbox message, so one must scroll back to it; cf. browser tabs that remember user web page position.
5. Respond to you
Current “intelligent” software tries to predict user wants but cannot itself take correction, e.g. Word’s auto-correct function changes i = 1 to I = 1, but if you change it back the software ignores your act. This software is clever enough to give corrections but not clever enough to take correction itself. However, responsive means responding to the user’s direction, not ignoring it.
The classic example of non-responsiveness was Mr. Clippy, Office 97’s paper clip assistant (Figure 4.3).

Searching the Internet for Mr. Clippy” at the time gave comments like “Die, Clippy, Die!” (Gauze, 2003), yet its Microsoft designer still wondered: “If you think the Assistant idea was bad, why exactly?”
The answer is as one user noted is: “It wouldn’t go away when you wanted it to. It interrupted rudely and broke your train of thought. (Pratley, 2004).
To interrupt inappropriately disturbs the user’s train of thought. For complex work like programming, even short interruptions cause a mental “core dump”, as the user drops one thing to attend to another. The interruption effect is then not just the interruption time, but also the recovery time (Jenkins, 2006); e.g. if it takes three minutes to refocus after an interruption, a one second interruption every three minutes can reduce productivity to zero. Mr Clippy was impolite, and this is why in XP it was replaced by side tags smart enough to know their place. In contrast to Mr Clippy, tag clouds and reputation systems illustrate software that reflects rather than directs online users.
Mr Clippy, like all selfish software, was oblivious to how the user sees it. Like Peter Sellers in the film “Being There”, selfish software likes to watch but cannot itself relate to others. Someone should explain to programmers that spying on a user is not a relationship. Mr. Clippy watched the user’s acts on the document, but could not see his interaction with the user, and so was oblivious to the rejection and scorn it evoked. It is a truism that most software today is less aware of its users than an airport toilet.
Selfish software, like a spoilt child, also repeatedly interrupts, e.g. a Windows Update that advises the user when it starts, as it progresses, and when it finishes. Such modal windows interrupt users, seize the cursor and lose current typing. Since each time the update only needs the user to press OK, it is like being repeatedly interrupted to pat a self-absorbed kiddie on the head. The lesson of Mr. Clippy, that software serves the person not the other way around, still needs to be learned.
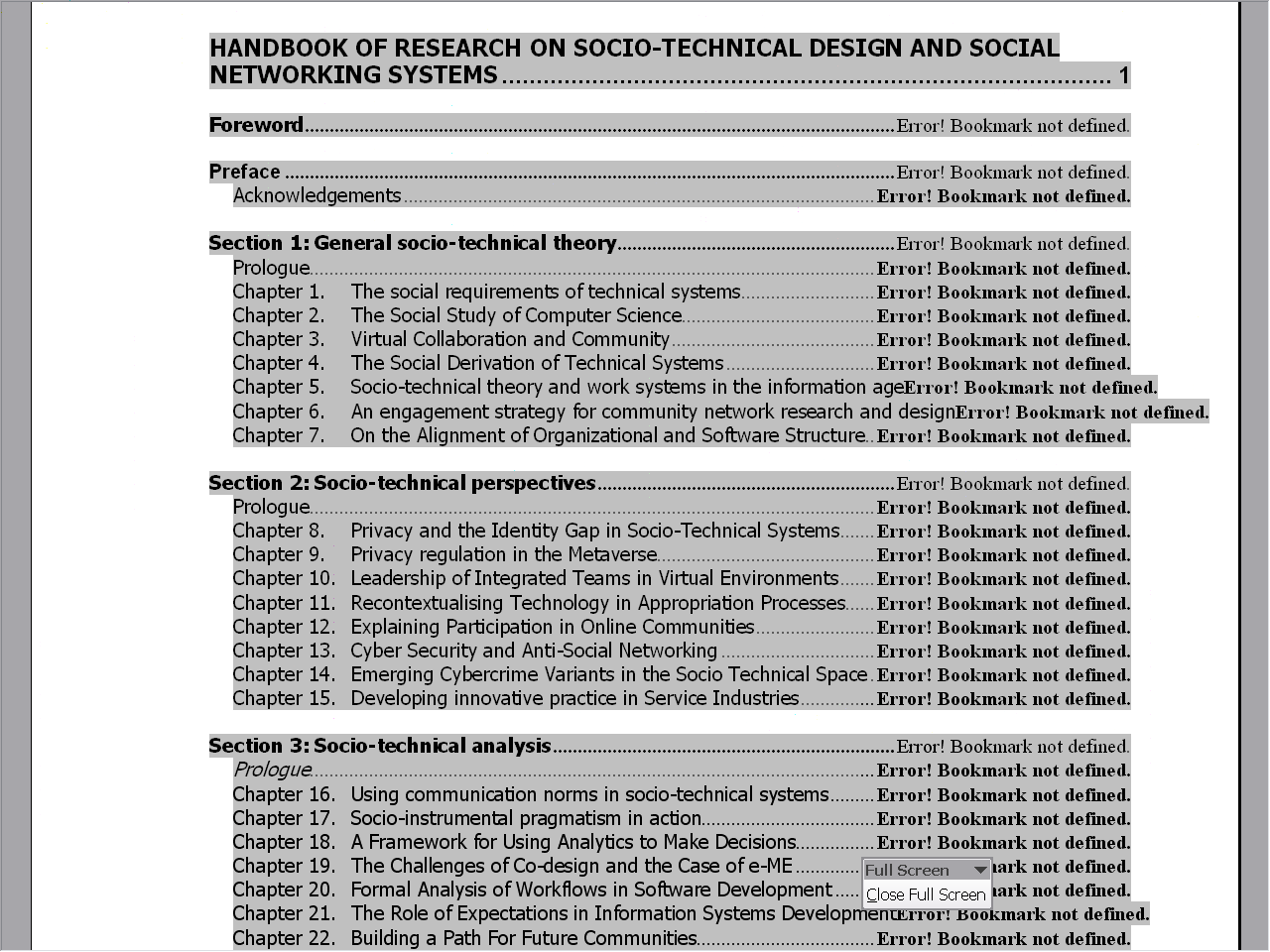
It is hard for selfish software to keep appropriately quiet; e.g. Word can generate a table of contents from a document’s headings. However if one sends just the first chapter of a book to someone, with the book’s table of contents (to show its scope), every table of contents heading line without a page number loudly declares: “ERROR! BOOKMARK NOT DEFINED”, which of course completely spoils the sample document impression (Figure 4.4). Even worse, this effect is not apparent until the document is received. Why could the software not just quietly put a blank instead of a page number? Why announce its needs so rudely? What counts is not what the software needs but what the user needs, and in this case the user needs the software to be quiet. The solution to such problems is polite computing.