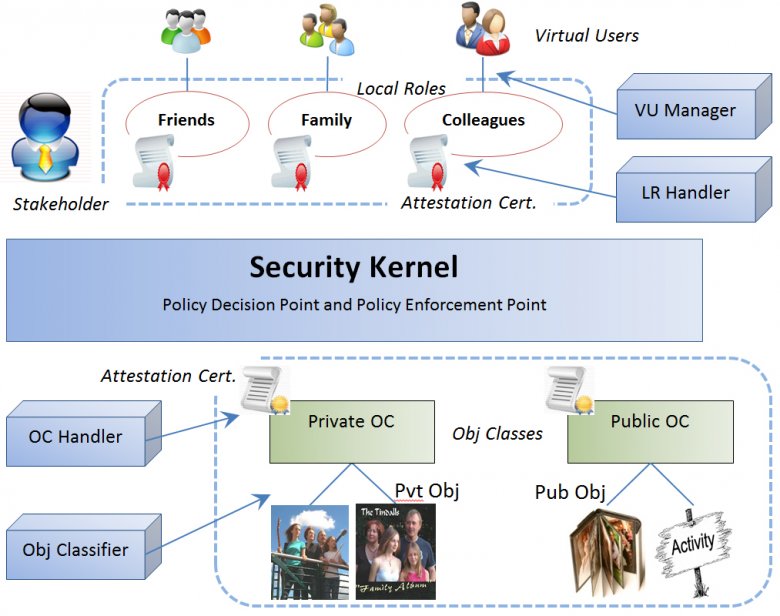
Traditional access control was based on a security kernel that checked every access request and decided if it was granted or denied based on a centralized access policy model. The person initiating the request then either saw it executed or got a “permission denied” message. As security was the focus, one decision point handled all requests.
Access control today is about distributing access. Social networks involve millions of people with billions of resources, so central control creates a bottle neck that slows the system down. In addition, people interacting on social media want local ownership for social reasons, as without this a community cannot develop. The focus has changed from security, or denying illegitimate access, to synergy, or allowing legitimate access. The aim is positive rather than negative. It requires the distribution of access control to local roles under the control of the people who create the resources. The access control rules outlined here aim to support the legitimate allocation of rights in an online social system. If distributed certificates of access are stored in the stakeholder’s namespace, only he or she can access and modify them (Figure 6.4).