Impolite computing has a long history. Spam is impolite because it takes choice away from email owners. Pop-up windows are impolite as they hijack the user’s cursor or point of focus. Changing your device settings without asking is impolite. Impolite computer programs:
1) Use your memory. Software that uses your hard drive to store information cookies or your phone service to download data without asking.
2) Change your settings. Software can change browser home page, email preferences or file associations.
3) Spy on what you do online. Spyware, stealthware and software back doors can gather information from your computer without your knowledge or record your mouse clicks as you surf the web, or even worse, give your private information to others.
For example, Microsoft’s Windows XP Media Player, was reported to quietly record the DVDs it played and use the user’s computer’s connection to “phone home”, i.e. send data back to Microsoft (Technology threats to Privacy, 2002). Such problems differ from security threats, where hackers or viruses break in to damage information. This problem concerns those we invite into our information home, not those who break in. A similar concern is “software bundling”, where users choose to install one product but are forced to get many:
“When we downloaded the beta version of Triton [AOL’s latest instant messenger software], we also got AOL Explorer – an Internet Explorer shell that opens full screen, to AOL’s AIM Today home page when you launch the IM client – as well as Plaxo Helper, an application that ties in with the Plaxo social-networking service. Triton also installed two programs that ran silently in the background even after we quit AIM and AOL Explorer.” (Larkin, 2005).
Yahoo’s “typical” installation of their IM also used to download their Search Toolbar, anti-spyware and anti-pop-up software, desktop and system tray shortcuts, as well as Yahoo Extras, which inserted Yahoo links on your browser, altered the user’s home page and made auto-search functions point to Yahoo by default. Even Yahoo employee Jeremy Zawodny disliked this:
“I don’t know which company started using this tactic, but it is becoming the standard procedure for lots of software out there. And it sucks. Leave my settings, preferences and desktop alone”. Jeremy Zawodny
Even today, many downloads require the user to opt-out rather than opt-in to offers. One must carefully review all the check boxes, lest one says something like: “Please send me endless spam on your products”.
A similar scheme is to use security updates to install new products, e.g. “Microsoft used the January 2007 security update to induce users to try Internet Explorer 7.0 whether they wanted to or not. But after discovering they had been involuntarily upgraded to the new browser, they next found that application incompatibility effectively cut them off from the Internet.” (Pallatto, 2007)
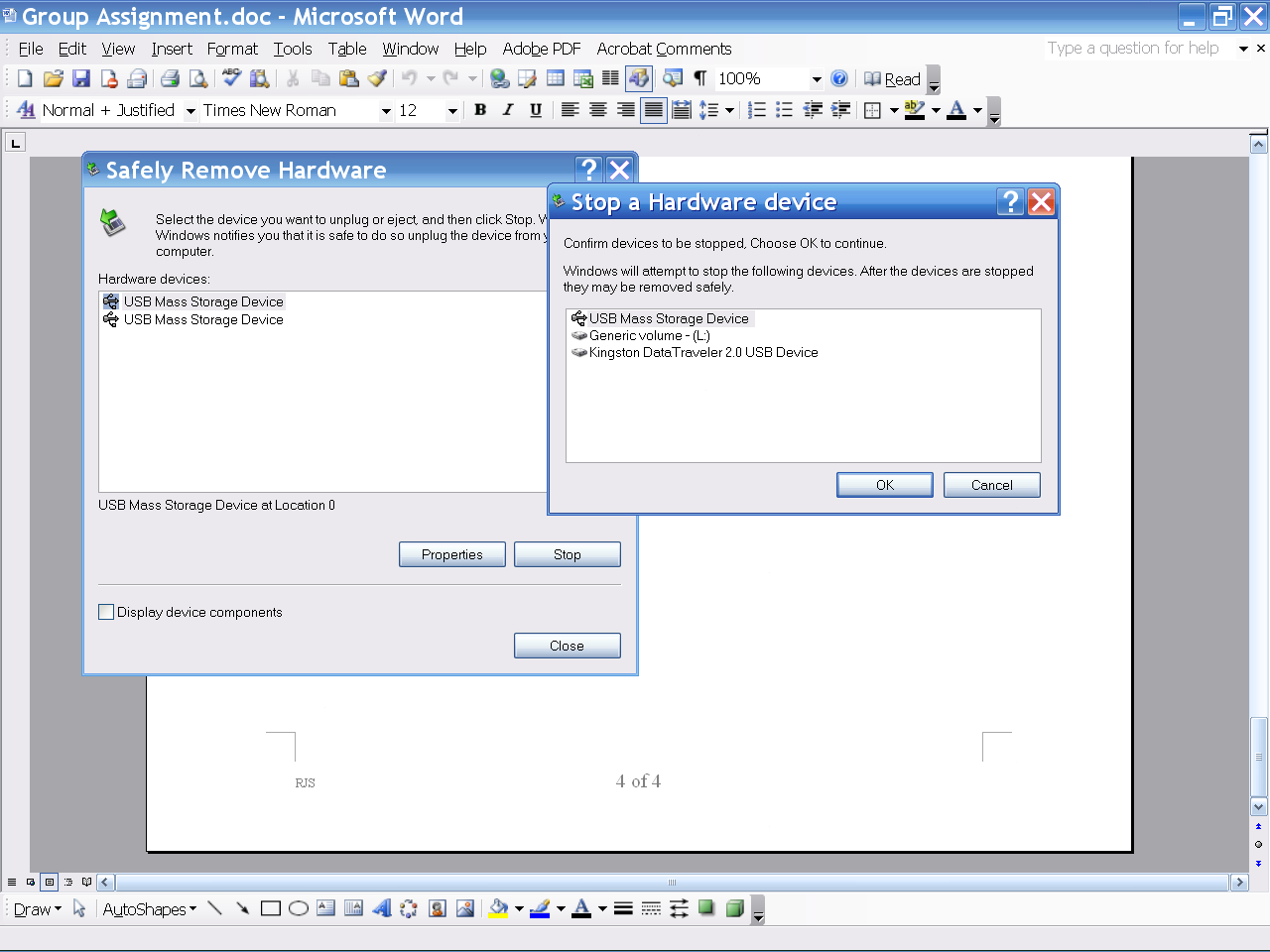
After installing Windows security update KB971033, many Windows 7 owners got a nag screen that their copy of Windows was not genuine, even though it was (Figure 4.5). Clicking the screen gave an option to purchase Windows (again). The update was silently installed – even with a Never check for updates setting, Windows did check online and installed it anyway. Despite the legitimacy principle that my PC belongs to me, Windows users found that Microsoft can unilaterally validate, alter or even shut down their software, by its End User License Agreement (EULA). As a result, people developed Windows hack tools like RemoveWAT. And Windows clients in general became more suspicious of their updates, while some chose to avoid Microsoft entirely and investigate more trustworthy options like Linux. A later study found that while 22% of computers failed the test, less than 0.5% had pirated software. Disrespecting and annoying honest customers while trying to catch thieves has never been a good business policy.
Security cannot defend against people one invites in, especially if the offender is the security system itself. However, in a connected society social influence can be very powerful. In physical society the withering looks given to the impolite are not toothless, as what others think of you affects how they behave towards you. In traditional societies banishment was often considered worse than a death sentence. An online company with a reputation for riding roughshod over user rights may find this is not good for business.
Blameware
Blameware is software that when things go wrong reports it as “your error”. It is interesting to compare messages when things are going well to times when they are not. While software seems delighted to be in charge in good times, when things go wrong it seems universally to agree that you have an error, not we have an error. Brusque and incomprehensible error messages like the “HTTP 404 – File not Found” suggest that you need to fix the problem you have clearly created. Although software itself often causes errors, some software designers recognize little obligation to give people information the software has in a useful form, let alone suggest solutions. To “take the praise and pass the blame” is not polite computing. Polite software sees all interactions as involving “we”. Indeed studies of users in human-computer tutorials show that users respond better to “Let’s click the Enter button” than to “Click the Enter button” (Mayer et al. 2006). When there is a problem, software should try to help the user, not blame them.
Pryware
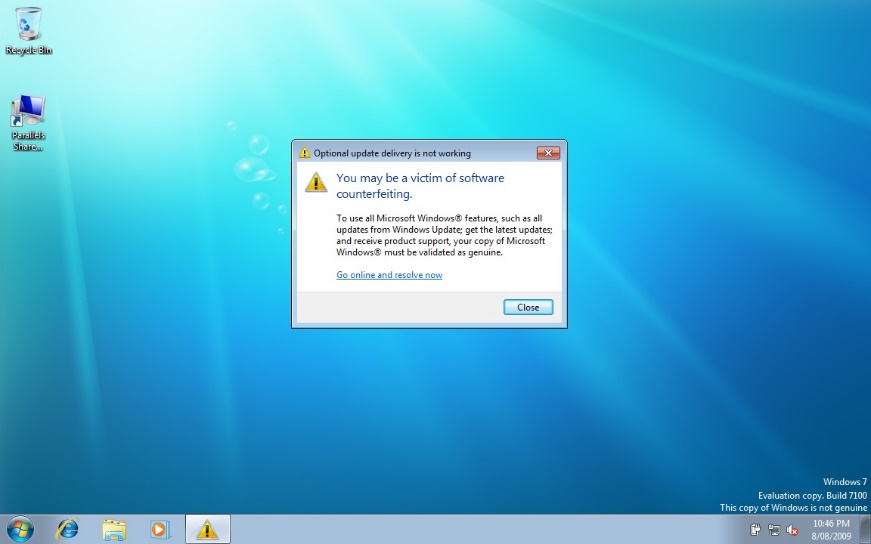
Pryware is software that asks for information it does not need for any reasonable purpose. Figure 4.6 shows a special interest site which wants people to register but for no obvious reason asks for their work phone number and job title. Some sites are even more intrusive, wanting to know your institution, work address and Skype telephone. Why? If such fields are mandatory rather than optional, people choose not to register, being generally unwilling to divulge data like home phone, cell phone and home address (Foreman & Whitworth, 2005). Equally, they may spam an address like “123 Mystreet, Hometown, zip code 246”. Polite software does not pry because intruding on another’s privacy is offensive.
Nagware
Nagware is software that keeps making the same request until you give in and agree. If the same question is asked over and over, for the same reply, this is to pester or nag, like the “Are we there yet?” of children on a car trip. It forces the other party to give again and again the same choice reply. Many users did not update to Windows Vista because of its reputation as nagware, that asked too many questions. Polite people do not bug others but software does, e.g. when reviewing email offline in Windows XP, actions like using Explorer triggered a “Do you want to connect?” request every few minutes. No matter how often one said “No!” it kept asking, because it had no memory of its own past. Yet in the past software has already solved this problem, e.g. uploading a batch of files creates a series of “Overwrite Y/N?” questions, which would force the user to reply repeatedly “Yes”, but there is a “Yes to All” meta-choice that remembers for the choice set. Such choices about choices (meta-choices) are polite. A general meta-choice console (GMCC) would give users a common place to see or set meta-choices (Whitworth, 2005).
Strikeware
Strikeware is software that executes a pre-emptive strike on user resources. An example is a zip extract product that, without asking, put all the files it extracted as icons on the desktop! Such software tends to be used only once. Installation programs are notorious for pre-emptive acts; e.g. the Real-One Player that added desktop icons and browser links, installed itself in the system tray and commandeered all video and sound file associations. Customers resent such invasions, which while not illegal are impolite. An installation program changing your PC settings is like furniture deliverers rearranging your house because they happen to be in it. Software upgrades continue the tradition; e.g. Internet Explorer upgrades that make MSN your browser home page without asking. Polite software does not do this.
Forgetware
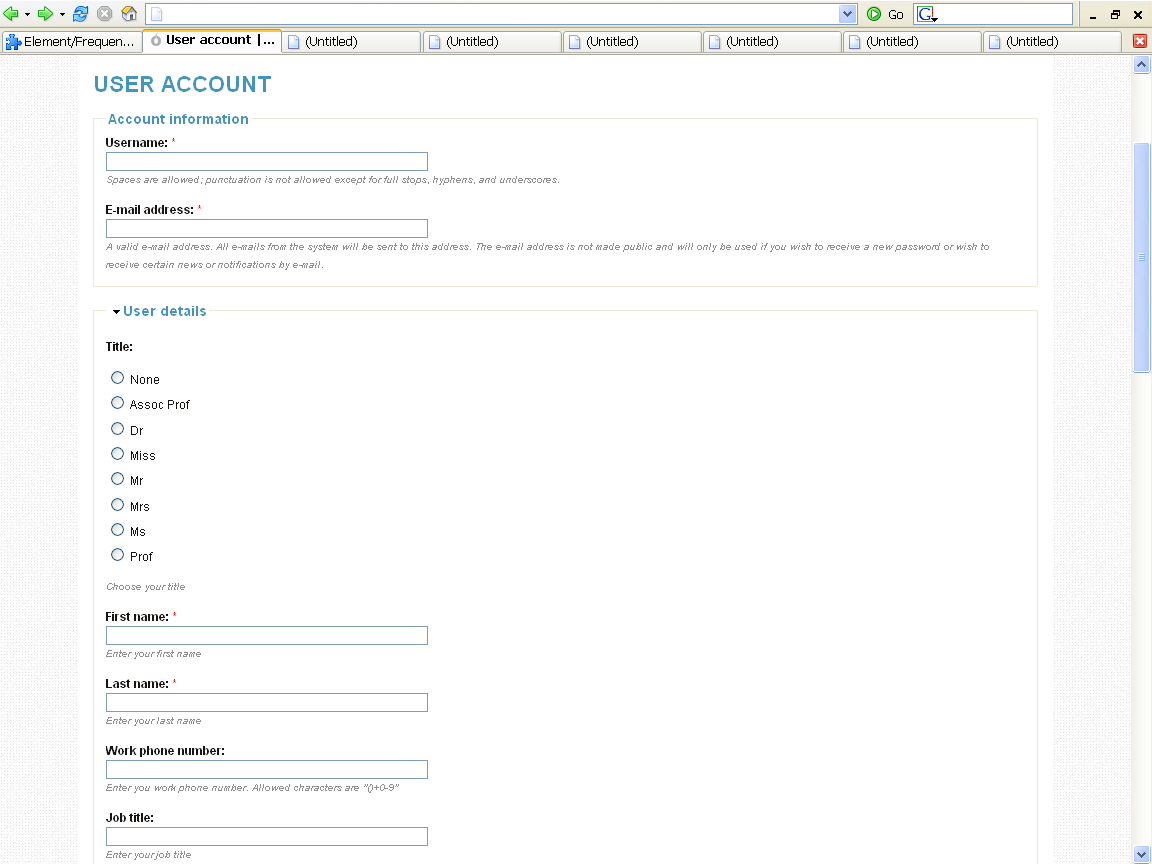
Forgetware is software that forgets every last thing you just told it. Its like talking to a person with amnesia. Working with Forgetware makes the simplest interaction hard; e.g. When you put a USB flash drive into a Windows XP computer it was so hard to get back, as you had to select it and stop it (Figure 4.7), and just pulling it out could corrupt its data. Imagine a human assistant that worked like this:
Boss: Hi Bill, please read this book for me (puts book in Bill’s left hand).
Assistant: Bill has found a book in his hand!
Boss: OK, I want the book back now, Bill.
Assistant: Should I safely remove the book in my left or right hand?
Boss: The book in your left hand, Bill. The one I just gave you.
Assistant: Please confirm the book you mean by pointing to it, or the hand, or both, and say “OK”. Then I will try to give it to you.
Boss: (points to left hand) OK!
Assistant: (left hand tries to give book but the right hand is holding it too) I can’t give the book to you right now; try again later.
Boss: Give me the book back!
Assistant: Do you want me to safely remove the book in my left hand or my right hand …
Boss: (grabs book and walks away.)
A human helper who acted like this would be insolent. If the Windows software can discover a USB is busy after the user selects it, why not check it before? Is its time more important than that of the user? Most users of course just check the USB drive light and if it is not flashing pull it out, avoiding all the above. In a similar vein, a computer voice reports my phone messages like this:
“There are five new messages. The first message received at 12.15pm on Wednesday the 14th of November is “<hang-up click>” To save this message press 1, to forward it press 3, to reply to it press 5, …, to delete it press 76.”
Note: “76” was the actual delete message code number, even though it is probably the most used option, especially for hang up calls. Again, imagine a human secretary who felt the need to report every detail of a call before telling you that the caller just hung up.